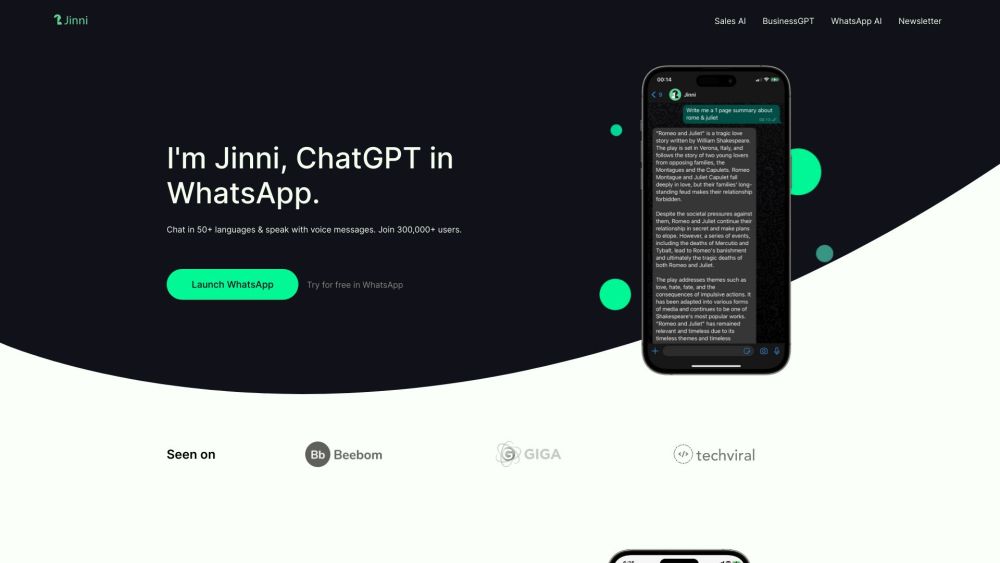
R1 Jailbreakers Discover Major Security Vulnerability in Rabbit's Code
Most people like
Discover the power of an AI-driven unified messaging platform that revolutionizes how businesses communicate. With seamless integration across multiple channels, this cutting-edge solution enhances collaboration and boosts productivity. Experience real-time connectivity, streamlined workflows, and personalized interactions, all in one intuitive interface. Embrace the future of messaging with an intelligent system designed to elevate your communication strategy and drive success.
Discover the power of our AI-driven platform designed to enhance your studying efficiency. With advanced algorithms and personalized strategies, this innovative tool empowers students to optimize their learning experience, boost retention, and achieve academic success. Transform the way you study today!
Find AI tools in YBX